People's Republic of China has been secretly obtaining classified data from servers of russian industrial sector enterprises, says CNews referring to a survey published by Kaspersky ICS CERT global cybersecurity research center.
It turns out that in January 2022, multiple Eastern European countries (incl. russia) and Afghanistan were attacked by a Chinese-speaking APT group TA428, which is known for previous similar campaigns against European and Asian enterprises, as the research suggests.
Read more: The russians Will "Remove" Cabins From Their Ural Trucks
The aim of the hacking was to hijack important classified data including ones regarding the projects developed by the defense industry, i.e. cyberspying.
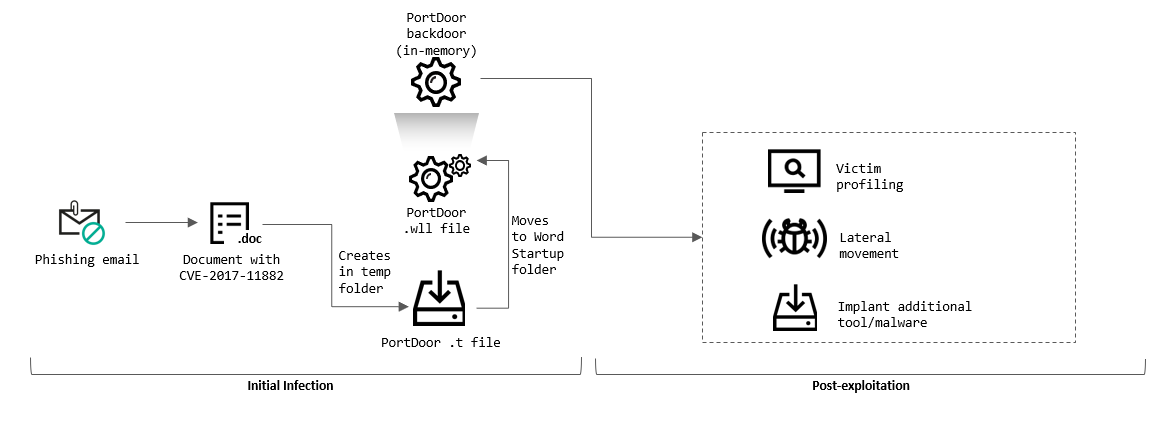
In practice, Chinese hackers used phishing emails to implant the PortDoor virus which, in turn, snatched the data. The attack consisted of two "echelons": the first echelon consisted of multiple servers in different countries, they transmitted the stolen files to the second-echelon server in China.
Analyst of the Ukrainian project "Information Resistance" Oleksandr Kovalenko highlighted that the TA428 group is backed by the PRC government which makes it twice as bitter, since russian state propaganda tries to portray russia and China to be "sacred brothers and the tandem of the century".
At the same time, Chinese TA428 has been spying on Russian ministries and departments, research institutes, government agencies of the Russian Federation and military-industrial complex enterprises:
"Remarkably, the Chinese hackers carried out their activities for several months, and therefore, one can only imagine how much secret information they got access to."

Another interesting detail about the attack is that the phishing emails intended to bait out the desired information, were "crafted using specific details on the organization’s operation, some of which may not be publicly available," as noted by Kaspersky center.
"An analysis of document metadata has shown that, with a high degree of likelihood, the attackers stole the document (while it was still legitimate) from another military industrial complex enterprise, after which they modified it using a weaponizer, a program designed to inject malicious code into documents," reads the survey.
Kaspersky ICS CERT doesn’t provide the list of enterprises affected by this hacking attack. Yet an expert asked by CNews assumes that the attacks were successful, as the report presented by Kaspersky indirectly implies.
Read more: We Have Sources in the Kremlin, but We Need Jets – Chief of the Defense Intelligence of Ukraine's MoD














