Another crucial piece of the puzzle has emerged to complete the picture of Operation Spiderweb, carried out by the Security Service of Ukraine deep in the rear of russia. The service has posted a video showing the full path covered by an individual manually operated FPV drone to the enemy airfield Belaya and the target — Tu-22M3 long-range bomber aircraft.
The footage presents what the operator of this drone was seeing throughout the entirety of the flight and starts from the drone's hiding place inside the truck parked near cafe Teremok. The location is the R255 federal highway, some 6 kilometers or nearly 3.7 miles from the military air base.
Read more: moscow Hides Its Tu-160 Strategic Bombers At Air Base 6,750 km from Ukraine
As the smoke in the distance suggests, it wasn't the first drone that took off for attack in that direction. This also shows that it wasn't a simultaneous swarm raid with dozens of drones trying to break to their targets all at once but a persistent lasting series of strikes. One possible explanation for preferring this tactic is that for operating the aerial vehicles, the local cellular network was used — with associated limitations on internet connection bandwidth.
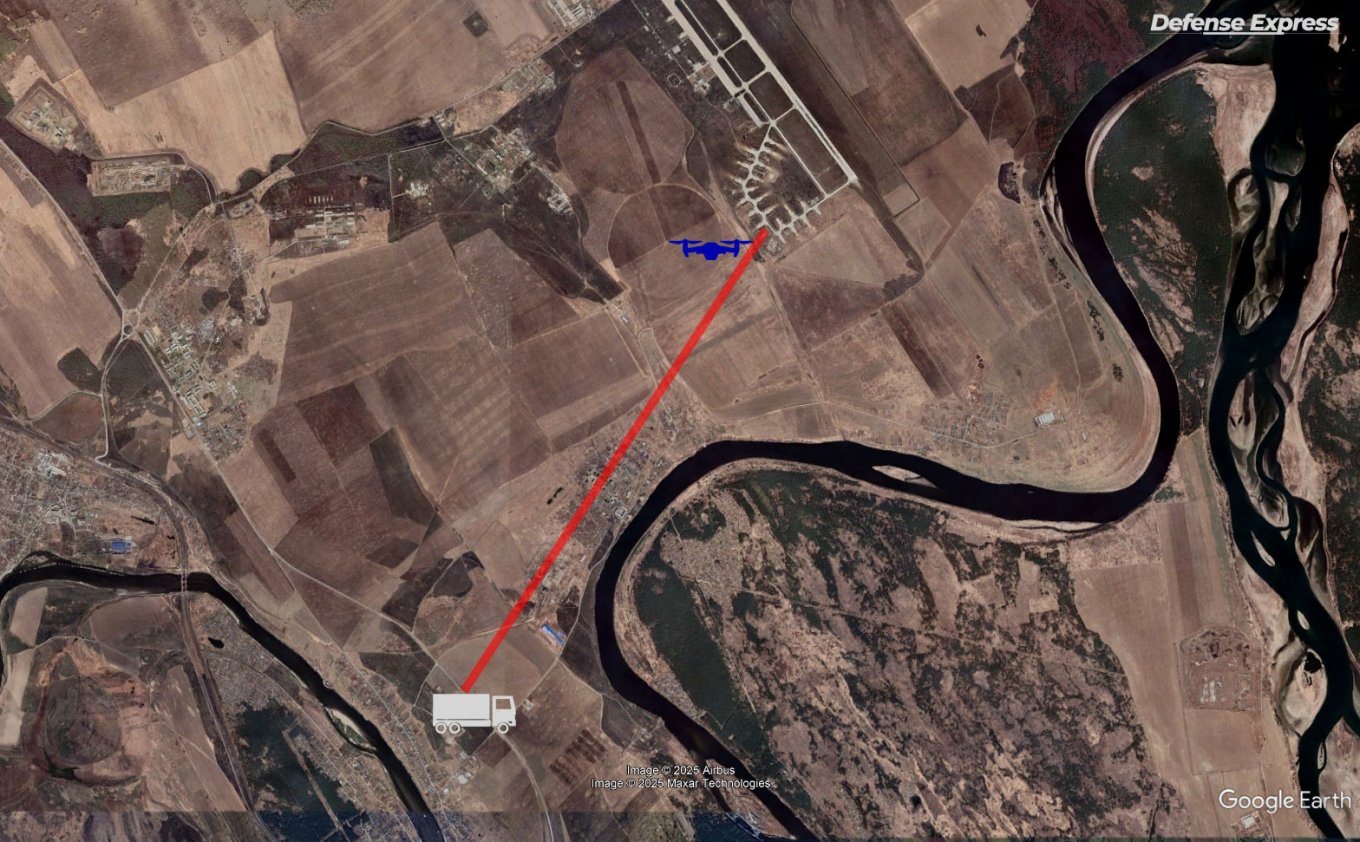
Another challenge was the strong wind from the side, as visible by the columns of smoke rising from the aircraft previously struck. The wind not only makes operating the drone more difficult, it also increases the time needed to cover the distance and drains the battery quickly.
Provided the First Contact Osa FPV drones were used for the mission, as Defense Express earlier assumed, with their battery endurance of 15 minutes midair in good weather, going against the wind could bite off much of spare time the operator had to finish the task or jeopardize it altogether.
Around halfway to the airfield, we can see the grass smoldering underneath: perhaps due to attempts by russian air defense to take down Ukrainian FPVs.

The journey to the airbase took about 6 minutes, then the drone hovered over the apron with Tu-22s, some already on fire. Instead of immediately going after the closest one, we can see the drone pilot reconnoiter the area and select the target carefully.

Only after that they direct the UAV towards a specific Tu-22M3. In particular, we can notice a special ladder the crew uses to get into the aircraft and other gear around. In satellite images, this bomber is not always in the same spot, indicating that it was a fully operational, active duty aircraft.

Next, the pilot attempts to hit the bomber in its most vulnerable spot — quite a task to achieve while controlling the drone via russian mobile internet from 5,000 km away in strong wind. According to the plan, the strike should land on the fuel tank above the wing root, where the tail is starting.
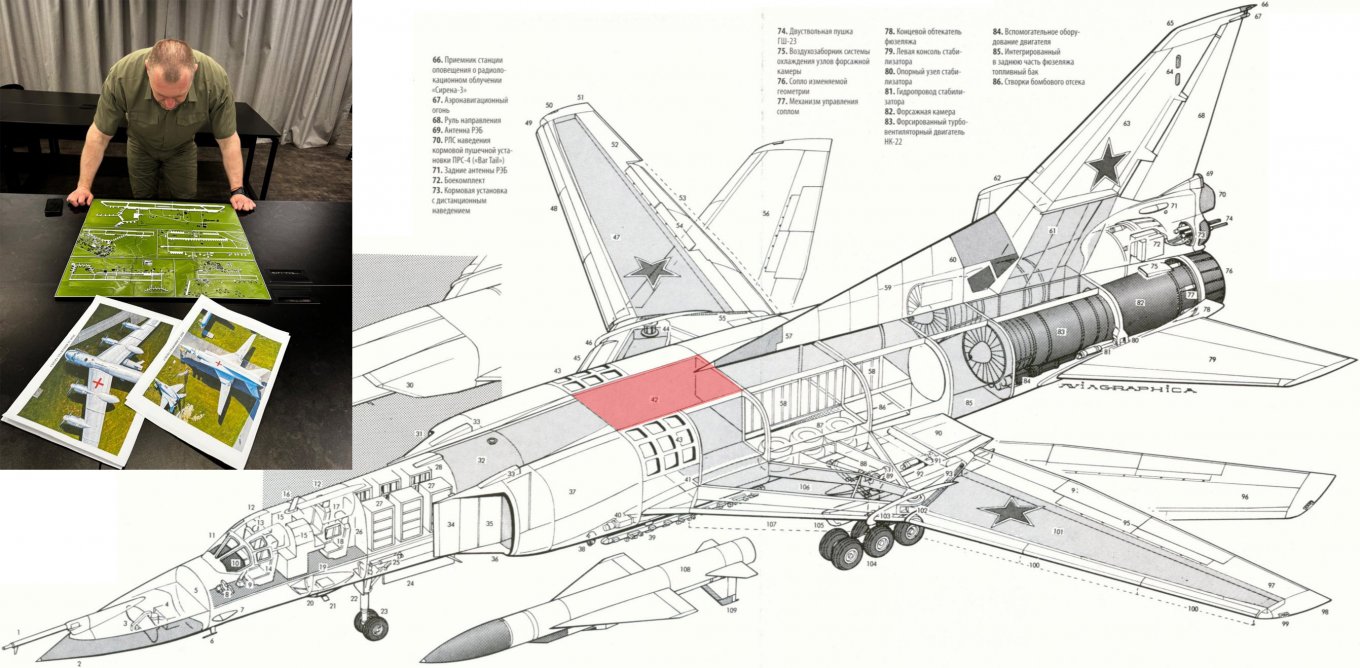
However, probably because of the wind and a big delay in communication (ping), the drone hits the Tu-22M3 not exactly in the intended segment of the fuselage but near the plane's dorsal fin. There's one of the smaller fuel tanks, too, and given the shaped charge warheads that the drones were equipped with, the impact should have cut the frames and other power elements of the aircraft.

Earlier, Defense Express elaborated on the vulnerable spots of Tu-22 and Tu-95 bombers and why precision in targeting them was crucial for the success of the mission. We also analyzed how many years and billions russia will need to restore Tu-160, Tu-95MSM and Tu-22M3 losses in this Ukrainian operation.
Read more: How Ukraine's FPV Drone Attack on Tu-95, Tu-22 Bombers Exemplifies McRaven’s 1993 Playbook














